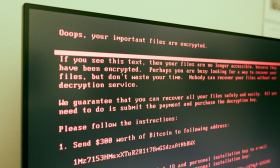
2018 was ‘a bad year’ for ransomware, but so far 2019 is no better

Local governments targeted by ransomware face a growing number of threats and continue to face severe challenges in undoing the damage caused by their attackers, federal and state officials told StateScoop.
Already in 2019, at least 22 state and local governments have been the victims of ransomware attacks. Baltimore was the most recent victim, where officials are in their third week of recovering computer systems that were encrypted by a virus known as RobbinHood, which has disabled numerous city functions including email, online bill payments and real estate transactions, hobbling the city’s housing market.
The hackers demanded 13 bitcoins — currently about $103,000 — which city officials have said they will not pay. Though one of the more severe and prolonged incidents in recent months, Baltimore’s experience is one that is becoming distressingly common for local governments around the country.
Speaking at a National Governors Association conference last week in Shreveport, Louisiana, Christopher Krebs, the director of the U.S. Department of Homeland Security’s Cybersecurity and Infrastructure Security Agency, called 2018 a “bad year” for state and local governments defending against ransomware threats. He also told StateScoop that there are more threats out there, likely inspired by the success of malware campaigns like the SamSam virus, which collected nearly $6 million in ransoms from more than 200 U.S.-based victims — including several local governments — over nearly three years.
“Eighteen was a successful year, and I think copycats and other hackers see opportunity out there,” he said.
‘Soft target’
Research published this month by the cybersecurity firm Recorded Future found that ransomware attacks against state and local governments rose 39 percent in 2018, with this year off to an active start. In March, Jackson County, Georgia, paid $400,000 to regain access to files and systems that had been frozen by Ryuk, a strain of ransomware that forced county agencies, including the sheriff’s office, to revert to conducting operations using pen and paper.
But paying the hackers — believed to be based in Eastern Europe — a vast sum for a decryption key did not put an end to the county’s concerns, even if it had restored access to its systems. Sam Blaney, the Georgia Technology Authority’s director of cybersecurity and risk compliance, said that by the time his office arrived to help the county of 60,000 people, its officials had already paid the ransom and started recovery efforts, but that there was still work to be done.
“We wanted to make sure they weren’t still a soft target,” Blaney said.
He said GTA got involved three weeks after the initial attack when county officials reached out through the Multi-State Information Sharing and Analysis Center, an organization used by state, local and tribal governments to exchange intelligence about cyberthreats.
“They had worked through some of their problems and wanted to have an independent look,” he said. “We suggested we continue with some recovery efforts and also get some third-party assistance.”
Blaney’s team found a company that is now helping Jackson County implement 20 controls and best practices issued by the Center for Information Security, the nonprofit research and intelligence organization that runs the MS-ISAC. Still, Blaney said if the county had contacted GTA before agreeing to pay the ransom, the state IT agency would’ve advised a different course of action.
“They went with the best counsel they had,” said David Allen, Georgia’s chief information security officer. “It sounds like they reached out to the appropriate parties and made a business decision.”
Allen said GTA is now relaying the incident to other local governments in Georgia, especially in rural areas. He said his team recently visited the regional association of county managers in northeastern Georgia, which includes Jackson, to urge them to take more preventative measures.
“We understand that you’re resource-constrained and you lack what you think you need to secure your networks,” Allen said he told the county managers. “There are resources like GTA, and through the MS-ISAC, we can help these counties.”
But Allen said the Jackson County incident showed that a local government’s cybersecurity has to be a concern for more than just the IT agency, especially in small communities. Some of the CIS controls address that, such as the creation of an interagency board to discuss information security matters.
‘Do the basics’
From the federal perspective, Krebs told StateScoop that there have been successful deterrence measures against ransomware, such as the indictment last November of two Iranian citizens for the SamSam operation, which has not been active since those charges were filed. But even with some of the tools that CISA can offer, such as cyber-hygiene assessments, there are still gaps that state and local governments can only address directly.
“You do have infrastructure that continues to be vulnerable,” Krebs said. “Legacy systems need to be retired. State legislatures are still lagging on [funding] IT investment and modernization. We continue engaging across government, but we just need folks to do the basics.”
In Baltimore, which spends $65 million on IT annually — barely half of what similarly sized cities spend, according to a 2018 planning document — officials have developed a few methods to restore some disrupted services, including a “manual workaround” for real-estate transactions using paper liens and in-person appointments at municipal offices that began Monday.
Citywide email, online bill payment and many other systems are still down, though. Baltimore officials are consulting with cybersecurity firms and the FBI, and, according to NPR, have reached out to their counterparts in Atlanta, which suffered a catastrophic attack in 2018 by the SamSam ransomware and has spent $17 million to recover from.
And it could be much longer until digital service in Baltimore is fully restored, Mayor Bernard C. “Jack” Young said Friday.
“I am not able to provide you with an exact timeline on when all systems will be restored,” he said in a city press release. “Like any large enterprise, we have thousands of systems and applications. You may see partial services beginning to restore within a matter of weeks, while some of our more intricate systems may take months in the recovery process.”